Introduction
Kubernetes is an open source production grade container orchestration system for deploying and managing docker/container applications. There are managed kubernetes orchestration service providers like Amazon Elastic Container Service for Kubernetes (EKS), Azure Kubernetes Service (AKS) etc.kubectl
Kubernetes cluster users can perform management tasks using kubectl binary which talks to API Server. Example kubectl commands# display pod resource
kubectl get pods -n my_namespace
# Execute a command in a container
kubectl -n my_namespace exec -it pods_name -- sh
# Listen on ports 5000 and 6000 locally, forwarding data to/from ports 5000 and 6000 in the pod
kubectl -n my_namespace port-forward pod/mypod 5000 6000
# Get output from ruby-container from pod my-pod-pd
kubectl attach my-pod-pd -c ruby-container
 |
| kubectl execution flow (source: 1ambda.github.io) |
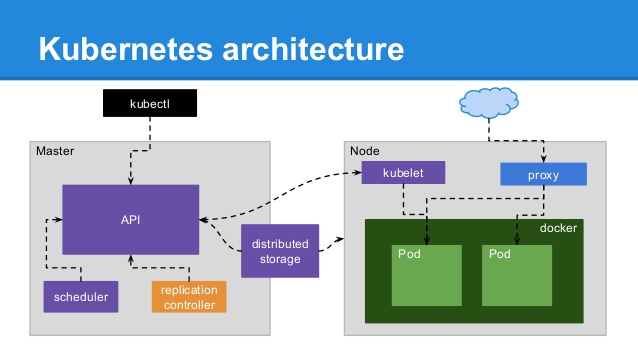
kubelet
kubelet, kube-proxy run's on each compute node (VM, Worker, EC2 Instance etc), kubelet listens on TCP port 10250 and 10255 (with no authentication/authorization). API Server acts as Reverse Proxy to kubelet and API Aggregation. API Server connects to the kubelet to fulfill commands like exec, port=forward and opens a websocket connection which connects stdin, stdout, or stderr to user’s original call [01].API Aggregation
Installing or writing additional API's into Kubernetes API Server i.e. extending core API ServerVulnerability
Vulnerability is in Kubernetes API Server, crafted request can execute arbitrary commands on the backend servers (pods) through the same channel client established to backend through API Server [02]
Check nodes Kubernetes version
$ kubectl get nodes -o wide NAME STATUS ROLES AGE VERSION INTERNAL-IP EXTERNAL-IP OS-IMAGE KERNEL-VERSION CONTAINER-RUNTIME
pd-worker-01 Ready node 13d v1.12.3 10.250.0.6
pd-worker-02 Ready node 13d v1.12.3 10.250.0.5
pd-worker-03 Ready node 13d v1.12.3 10.250.0.4
Vulnerable API Servers
If API server response looks as bellow and using vulnerable API versions of Kubernetes the you are vulnerable using anonymous-user escalation, patch Kubernetes immediately.HTTP response error code 403 indicates Forbidden i.e. related to Authorization implies we successfully passed through Authentication phase.
{ "kind": "Status", "apiVersion": "v1", "metadata": { }, "status": "Failure", "message": "forbidden: User \"system:anonymous\" cannot get path \"/api/v1/\"", "reason": "Forbidden", "details": { }, "code": 403 }
anonymous user
By default, requests to the kubelet’s HTTPS endpoint that are not rejected by other configured authentication methods are treated as anonymous requests, and given a username of system:anonymous and a group of system:unauthenticated.Mitigations
There are three levels of escalation mitigations1. anonymous user -> aggregated API server
API Server admission-controller parameter anonymous-auth is set to fault
$ kubectl get po kube-apiserver-01 -n prod -o yaml | grep -i "anonymous-auth" - --anonymous-auth=false
$ kubectl get po kube-apiserver-01 -n stage -o yaml | grep -i "anonymous-auth" - --anonymous-auth=false
$ kubectl get po kube-apiserver-01 -n stage -o yaml | grep -i "anonymous-auth" - --anonymous-auth=false
2. authenticated user -> aggregated API server
Suspend aggregated API servers usage3. authorized pod exec/attach/portforward -> kubelet API
Remove pod exec/attach/portforward permissions for usersReferences
[01]. https://docs.openshift.com/container-platform/3.11/architecture/networking/remote_commands.html[02]. https://docs.openshift.com/container-platform/3.11/architecture/networking/remote_commands.html
[03]. https://elastisys.com/2018/12/04/kubernetes-critical-security-flaw-cve-2018-1002105/
[04]. https://github.com/kubernetes/kubernetes/issues/71411
I am glad that I have visited your blog, really amazing. Waiting for further updates.
ReplyDeleteccna course in Chennai
ccna Training in Chennai
AngularJS Training in Chennai
Ethical Hacking course in Chennai
PHP Training in Chennai
gst training in Chennai
Tally Classes in Chennai
ui ux design course in Chennai
ccna course in anna nagar
Delete☑️☑️COMPOSITE CYBER SECURITY SPECIALISTS ☑️☑️
•• Are you Seeking for the Best Legit Professional Hackers online?
Congratulations Your search ends right here with us. •• ⚡️⚡️
☑️☑️For Years Now We have Been helping companies secure there Infrastructures against malicious Attacks, however private individuals have been making use of our services to provide Optimum solutions to their cyber and Hacking related Issues by providing them unlimited Access to their desired informations from their Target such as Phone Hack (Which enables them to monitor their kids/wife/husband/boyfriend/girlfriend, by gaining access to everything they are doing on their phone without their notice), Credit Card Mishaps, Website Hacking, Funds Recoveries And Every Other Cyber Related Issues That has to Do With HACKING.
☑️☑️COMPOSITE CYBER SECURITY SPECIALISTS is a vibrant squad of dedicated online hackers maintaining the highest standards and unparalleled professionalism in every aspect.
We Are One Of The Leading Hack Teams In The United States With So Much Accolades From The Deep Web And IT Companies. ••
••We Offer Varieties Of LEGIT Hacking Services With the Help Of Our Root HackTools, Special HackTools and Our Technical Hacking Strategies Which Surpasses All Other Hackers.
☑️ Below Is A Full List Of Our Services:
▪️ FUNDS RECOVERY ON SCAM INVESTMENTS, BINARY OPTIONS TRADING and ALL TYPES OF SCAMS.
▪️ WEBSITE AND DATABASE HACKING 💻
▪️ CREDIT REPAIR. 💳
▪️ PHONE HACKING & CLONING (giving you 📱 Unnoticeable access to everything Happening on the Target’s Phone)
▪️ CLEARING OF CRIMINAL RECORDS ❌
▪️ SOCIAL MEDIA ACCOUNTS HACKING 📱
▪️RECOVERY OF DELETED FILES 📤
▪️LOCATION TRACKING 📌
▪️BITCOIN MINING ⛏ And lot More.
☑️We have a team of seasoned PROFESSIONALS under various skillsets when it comes to online hacking services. Our company in fact houses a separate group of specialists who are productively focussed and established authorities in different platforms. They hail from a proven track record and have cracked even the toughest of barriers to intrude and capture all relevant data needed by our Clients. Some Of These Specialist Includes ⭐️ DAWID CZAGAN⭐️ JACK CABLE ⭐️ SEAN MELIA ⭐️ ARNE SWINNEN ⭐️And More. All you Need To do is To Write us a Mail Then We’ll Assign any of These Hackers To You Instantly.
☑️COMPOSITE CYBER SECURITY SPECIALISTS is available for customer care 24/7. Feel Free to Place your Requests.
☑️☑️CONTACT:
••• Email:
composite.cybersecurity@protonmail.com
🔘2020 © composite cybersecurity specialists
🔘Want faster service? Contact us!
🔘All Rights Reserved ®️.
I am definitely enjoying your website. You definitely have some great insight and great stories. outdoor security camera
ReplyDeleteI am glad that I saw this post. It is informative blog for us and we need this type of blog thanks for share this blog, Keep posting such instructional blogs..lovely post guys...
ReplyDeleteAngularJS training in chennai | AngularJS training in anna nagar | AngularJS training in omr | AngularJS training in porur | AngularJS training in tambaram | AngularJS training in velachery
I love to read your articles because your writing style is too good, its is very very helpful for all. they are becomes a more and more interesting from the starting lines until the end.Share more like this.
ReplyDeleteCyber Security Training Course in Chennai | Certification | Cyber Security Online Training Course| Ethical Hacking Training Course in Chennai | Certification | Ethical Hacking Online Training Course| CCNA Training Course in Chennai | Certification | CCNA Online Training Course| RPA Robotic Process Automation Training Course in Chennai | Certification | RPA Training Course Chennai| SEO Training in Chennai | Certification | SEO Online Training Course
Are you interested in any kinds of hacking services?
ReplyDeleteFeel free to contact TECHNECHHACKS.
For years now we’ve helped so many organizations and companies in hacking services.
TECHNECHHACKS is a team of certified hackers that has their own specialty and they are five star rated hackers.
We give out jobs to hackers (gurus only) to those willing to work, with or without a degree, to speed up the availability of time given to jobs!!
Thus an online binary decoding exam will be set for those who needs employment under the teams establishment.
we deal with the total functioning of sites like,
• SOCIAL MEDIA (Facebook, Twitter, Instagram, Snapchat, google hangout etc.)
• SCHOOL GRADES
• IOS/OS
• CREDIT SCORES
• BANK ACCOUNTS
• SPOUSES PHONE
Our special agents are five star rated agents that specializes in the following, and will specially be assigned to you for a special job well DONE.
• WESTERN UNION TRANSFER
• CREDIT CARDS INSTALLATION
• MONEY FLIPPING
• CRIMINAL RECORDS
• BTC RECOVERY
• BTC MINING
• BTC INVESTMENT
Thus bewere of scammers because most persons are been scammed and they ended up getting all solutions to their cyber bullies and attacks by US.
I am Jason williams one of the leading hack agent.
PURPOSE IS TO GET YOUR JOBS DONE AT EXACTLY NEEDED TIME REQUESTED!!!
And our WORK SUCCESS IS 100%!!!
We’re always available for you when you need help.
Contact or write us on:
Technechhacks@gmail.com
SIGNED....!
Jason. W
TECHNECHHACKS
2021©️All Right Reserved
It is optional towards connect/promotion Windows 7 your existing type of Spaces successively. You hunger a fresh connection of Gaps scheduled a laptop, you necessity towards set-up the solid ambition and reinstall the spaces using it’s invention significant. Windows 7 Professional Product Key Free
ReplyDeleteReimage Pc Repair Crack is a program that solves hardware problems like low memory, low disk speed, temperature, and even CPU power. Free Reimage Repair
ReplyDeleteMotivational Quotes Good Morning Status Image. Truly Inspirational Good Morning Messages and Quotes for FREE.Wishing someone good morning with a beautiful quote .Good Morning Wishes Text
ReplyDelete