Wireshark/Ethereal is one of the best open source tools we have. I don't think there will be individuals working in Networking domain (especially into IDS/IPS, Firewalls etc.) and don't know Wireshark/tcpdump. Please I wanna see u guys/gals ;-)
There are many features available in Wireshark, we are going to focus on remote packet capture.
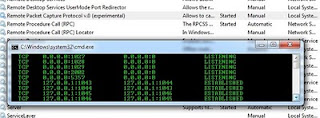
Need Wireshark Version 1.4.2 with the new WinPcap available inbuilt with it. Install this on bothe the machines, where you are going to take capture (client) and on the machine where we want to sniff the traffic(server). On Server we need to start "Remote Packet Capture Protocol v.0 (experimental)" service, which will open TCP Port 2002 on the Server.
There are many features available in Wireshark, we are going to focus on remote packet capture.
Need Wireshark Version 1.4.2 with the new WinPcap available inbuilt with it. Install this on bothe the machines, where you are going to take capture (client) and on the machine where we want to sniff the traffic(server). On Server we need to start "Remote Packet Capture Protocol v.0 (experimental)" service, which will open TCP Port 2002 on the Server.
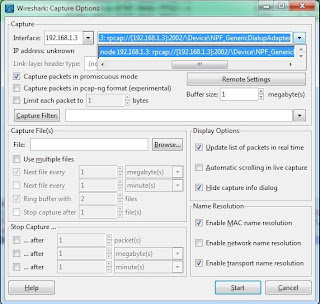
Once the service is started, run wireshark on the Client machine. Goto Capture->Options. Clicking Options will pop up a window shown below.
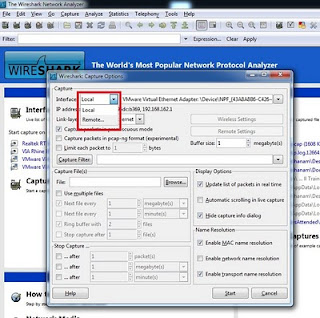
In this window we can see Interface field on the top left corner which has drop down menu, from this menu select "Remote" option which will pop one more window asking for details like Host: (Enter IP Address), Port:, enter 2002 here.
Authentication:
For logging onto Server to take packet capture we need to successfully authenticate to server.
Authentication:
For logging onto Server to take packet capture we need to successfully authenticate to server.
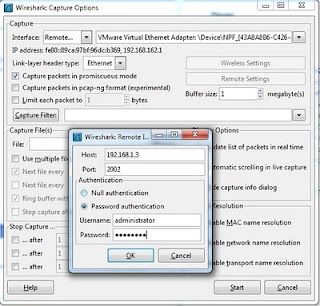
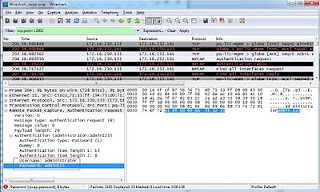
Under Authentication, opt for Password authentication, Null authentication is not supported which might throw below error.
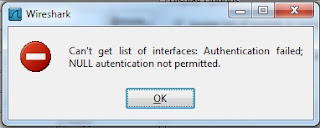
Once the Authentication is successfull you can select one of the interfaces on the Server if there are multiple for sniffing.
Security:
Well, this is one of the awesome features Wireshark has given to its users. But the downside is, log in credentials traversing the network in clear text. Atleast they would have provided basic encryption/ encoding techniques to hide password.
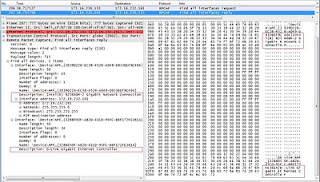
Exposing all the interfaces of a multi homed Server, it's IP Addresses etc.
Hope this post and feature will be very helpful for you :-)
Following articles might be of your interest
http://darshanams.blogspot.in/2012/05/cain-and-abel-password-cracking.html
http://darshanams.blogspot.in/2011/09/portable-document-files.html
http://darshanams.blogspot.in/2010/09/forensics-1-extracting-image.html
http://darshanams.blogspot.in/2011/05/snort-logging-alerts-to-syslog-server.html














